Listen now
Modern manufacturers win and lose based on their ability to orchestrate complex and disparate processes across an increasingly automated landscape of IoT devices and robots. The success of an assembly line is measured on its productivity, and the more efficient they get, the more critical uptime becomes. For the typical auto manufacturer today, one hour of downtime costs $2.3 million, over twice as much as that hour would have cost just five years ago.
Siemens predicts that unplanned downtime now costs the Global 500 over 11% of revenues or $1.4 trillion globally, highlighting a sobering reality: the need for securing operational technology (OT) from cyberattacks is no longer just an IT afterthought—it’s a strategic, existential imperative.
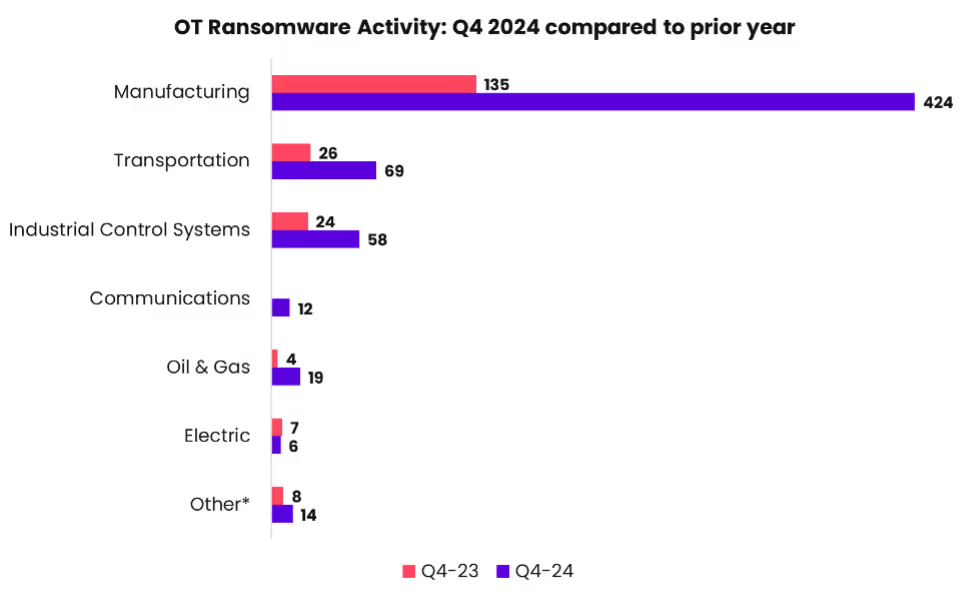
This reality isn’t isolated. The shop floor has become the newest attack vector. In Q4 2024, Dragos reported manufacturing alone experienced a staggering 308 ransomware attacks on critical infrastructure, accounting for more than half of global OT cyberattacks. The urgency is undeniable, and attackers are aggressively targeting these vulnerabilities. Factories, utilities, and transport hubs must adopt new security platforms that reach beyond the OS into the firmware and device layers.
At NGP Capital, we've been excited about backing founders who are transforming this intersection through our convergence thesis, shaped by investments across both industrial automation and cybersecurity. This convergence—the interweaving of digital and physical security—is rapidly becoming the new frontline in safeguarding industrial resilience.
Why Now?
Four powerful trends are converging, elevating OT cybers from a peripheral concern to a core function of enterprise security:
Reshoring and Industrial Revival: Rising geopolitical tensions and supply chain disruptions have accelerated reshoring efforts to Western economies, driven by domestic incentives and tariff uncertainty. Today, downtime is not just operationally disruptive, it’s economically disastrous and a potential risk to national security.
Geopolitical Cyber Warfare: Cyberattacks have transcended espionage, becoming instruments of geopolitical leverage, as demonstrated by recent warfare in Ukraine and Iran, attacks on U.S. power grids, and attempted disruptions at Taiwanese semiconductor plants. Critical infrastructure is now seen as the weak link within corporate defenses, and bad actors have shifted their strategy to target these environments.
Regulatory Surge: New legislation is reshaping global standards for protecting industrial assets. The EU’s NIS2 Directive and US’ Pipeline Security Directive in wake of the Colonial Pipeline attack (TSA's) mandate stricter cyber controls. Regulators are now requiring comprehensive monitoring and reporting for OT systems.
Rising OT Complexity Expands the Attack Surface: Industrial leaders are aggressively investing in digitization and automation to scale domestic production and meet demand. The rising complexity, volume, and criticality of robotics and connected intelligence have significantly expanded the OT attack surface, blurring traditional IT/OT boundaries.
Current Landscape of OT Security
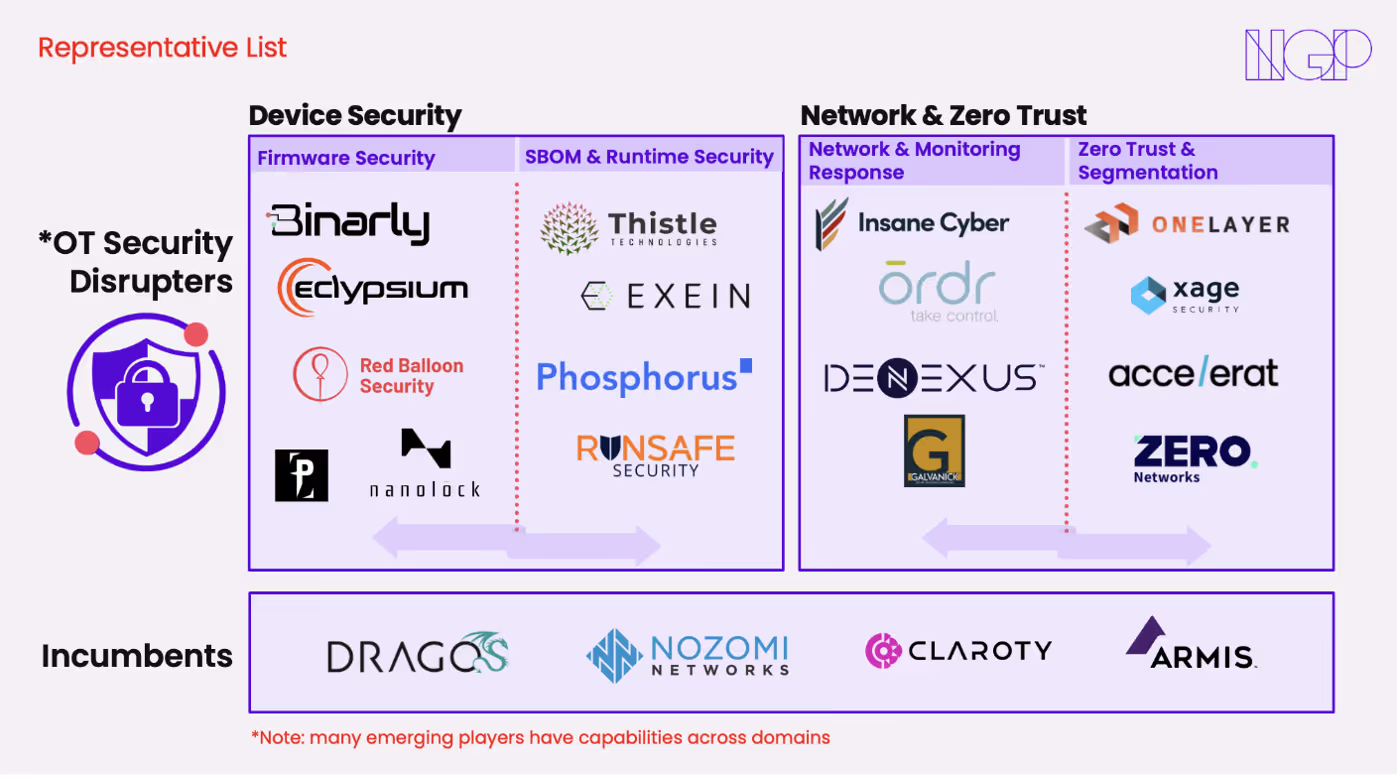
Although OT security is rapidly maturing, several large incumbents have already emerged. Early leaders like Vdoo (acquired by JFrog), Nozomi Networks, Claroty, and Dragos validated the scale of the market opportunity, but their solutions have primarily relied on passive, network-level monitoring. Like doctors limited to observing surface-level symptoms, these incumbents lack deeper diagnostic capabilities. This gap has created an opening for the next generation of startups who specialize in active, device-level inspection and prevention.
Today, the current landscape of OT security can be broadly categorized into two key segments with new subsegments emerging:
1. Device Security: This encompasses securing endpoints such as programmable logic controllers (PLCs), IoT sensors, and internet-connected industrial devices:
- SBOM & runtime security actively scans and monitors devices for vulnerabilities, ensuring operational integrity across device families. These platforms can detect and respond to anomalies in real-time, minimizing the impact of potential breaches.
- Firmware security targets protection against persistent threats embedded deeply within device firmware. Ensuring firmware integrity through continuous monitoring, secure boot procedures, and authenticated updates is essential to maintain resilience against persistent and often undetected threats.
2. Network Security: Network security safeguards the communication channels and infrastructure connecting these devices, typically through solutions like network monitoring, segmentation, and enhanced threat visibility.
- Network monitoring and response involves continuous analysis of network traffic to detect threats and anomalies. Capabilities typically include real-time monitoring, anomaly detection, threat intelligence integration, and automated or guided responses, exemplified by solutions from companies like Dragos and Nozomi Networks.
- Zero-trust and segmentation ensure devices operate within clearly defined parameters, restricting unauthorized access and changes. Segmentation further isolates devices, limiting potential attack impacts and enhancing operational resilience.
Emerging Themes and Opportunities
A number of forces are quietly rewriting the OT-security playbook. Firmware has become the invisible frontline where attackers gain persistent footholds beneath traditional security layers, while IT/OT network convergence is breaking down security silos and demanding tighter integration. Evolving regulatory frameworks are making secure lifecycle management mandatory, and explosive OT data growth is driving demand for AI-powered edge security in resource-constrained environments or devices. Most concerning, recent supply chain attacks have exposed deep vulnerabilities in third-party components that were left unmonitored.
These trends create compelling opportunities for new approaches that address foundational gaps in our increasingly connected industrial infrastructure:
Target Firmware and Device Security: Solutions that monitor and secure layers beneath the network layer and OS will carve out enterprise wallet share as legacy tools fail to spot threats buried in silicon and machine code.
Extend OT into the IT Domain: Prioritize solutions that cohesively unite and extend traditional IT capabilities (identity, zero-trust, security analytics) to OT assets. This greatly reduces the friction between IT and OT when deploying security capabilities and addresses the expanded and interconnected nature of modern OT environments.
Demonstrate Operational ROI: Solutions demonstrating quantifiable reductions in downtime as well as risk will resonate most strongly with corporate decision-makers, particularly in the wake of recent attacks. By bringing higher levels or visibility and orchestration to OT assets, new players can prove ROI not only through mitigating cyber risk but revenue driving activities like down time reduction.
Adopt an AI-Native Approach: As the skilled labor gap widens and alert volume soars, manual triage has become unsustainable. Platforms that embed AI-native architectures can take advantage of best-in-class models to automatically detect, prioritize, and orchestrate remediation actions. Founders who build these AI-first capabilities from day one will outpace incumbents retrofitting legacy stacks.
Looking Ahead
The next news-worthy breach may start silently in the firmware of critical hardware, propagate across private OT networks, and cause catastrophic downtime. The landscape has changed irreversibly: OT security now defines operational continuity, corporate resilience, and competitive advantage.
This inflection point is rich with opportunity. For visionary founders, now is the time to build the cyber technologies that will define the industrial landscape for decades. If you’re building in the space, I would love to chat—reach out to eric@ngpcap.com!

.svg)






.svg)





.avif)



